5 Cyber Ops Tips

Introduction to Cyber Operations

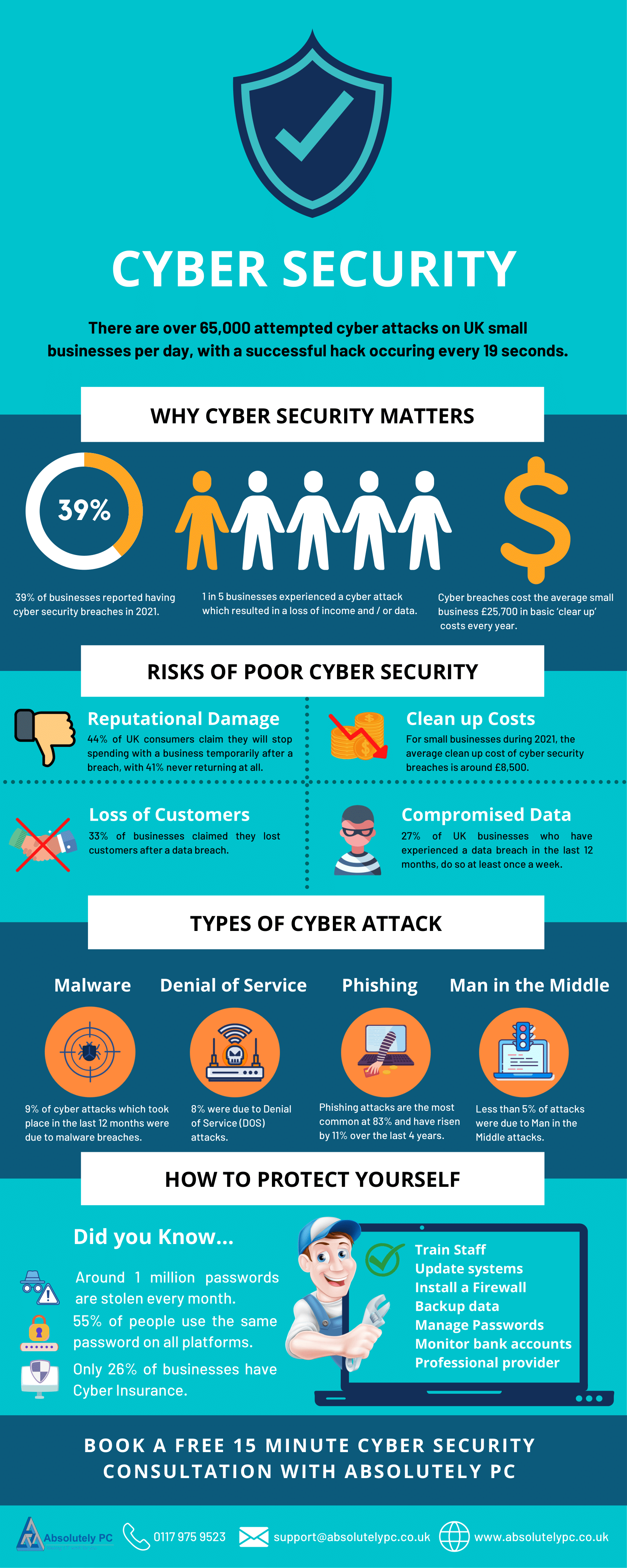
In the realm of cybersecurity, cyber operations play a critical role in protecting networks, systems, and infrastructure from cyber threats. As the world becomes increasingly dependent on digital technologies, the importance of robust cyber defenses cannot be overstated. This post will delve into the world of cyber ops, providing valuable insights and tips for those looking to enhance their cybersecurity posture.
Understanding Cyber Ops

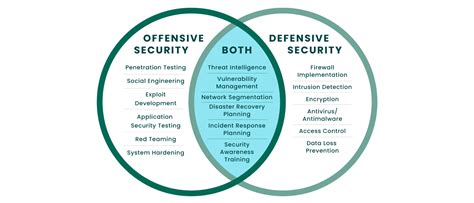
Cyber operations encompass a broad range of activities, including threat hunting, incident response, and vulnerability management. These operations are designed to identify, mitigate, and remediate cyber threats, ensuring the confidentiality, integrity, and availability of sensitive data and systems. Effective cyber ops require a deep understanding of the cyber threat landscape, as well as the latest tools and techniques used by adversaries.
Cyber Ops Tips

Here are five essential tips for improving your cyber operations: * Implement a robust threat intelligence program: Stay informed about the latest cyber threats and trends, and use this intelligence to inform your security decisions. * Conduct regular vulnerability assessments: Identify and remediate vulnerabilities in your systems and networks to prevent exploitation by attackers. * Develop an incident response plan: Establish a plan for responding to cyber incidents, including procedures for containment, eradication, recovery, and post-incident activities. * Invest in security orchestration, automation, and response (SOAR) tools: Leverage SOAR tools to streamline and automate your security operations, improving efficiency and reducing the risk of human error. * Provide ongoing training and awareness programs: Educate your personnel on the latest cyber threats and best practices, ensuring they are equipped to handle the evolving cyber landscape.
Cyber Ops Tools and Technologies

A range of tools and technologies are available to support cyber operations, including:
| Tool/Technology | Description |
|---|---|
| Security Information and Event Management (SIEM) systems | Collect, monitor, and analyze security-related data from various sources |
| Intrusion Detection Systems (IDS) | Identify and alert on potential security threats in real-time |
| Incident Response Platforms | Streamline and automate incident response processes |
🚨 Note: The effectiveness of cyber ops tools and technologies depends on proper configuration, maintenance, and ongoing monitoring.
Best Practices for Cyber Ops

To ensure the success of your cyber operations, consider the following best practices: * Continuously monitor and analyze security-related data: Stay vigilant and proactive in identifying potential security threats. * Implement a defense-in-depth approach: Layer multiple security controls to protect against various types of attacks. * Foster collaboration and information sharing: Work with other teams, organizations, and industries to stay informed and share best practices. * Stay up-to-date with the latest cyber threats and trends: Participate in training, conferences, and online forums to stay current and knowledgeable.
Conclusion and Final Thoughts

In the ever-evolving world of cybersecurity, effective cyber operations are crucial for protecting against cyber threats. By implementing robust threat intelligence programs, conducting regular vulnerability assessments, and leveraging the latest tools and technologies, organizations can improve their cybersecurity posture and reduce the risk of cyber incidents. Remember to stay vigilant, proactive, and informed, and always be prepared to adapt to the changing cyber landscape.
What is the primary goal of cyber operations?

+
The primary goal of cyber operations is to protect networks, systems, and infrastructure from cyber threats, ensuring the confidentiality, integrity, and availability of sensitive data and systems.
What is threat intelligence, and how is it used in cyber ops?
+
Threat intelligence refers to the collection, analysis, and dissemination of information about potential cyber threats. In cyber ops, threat intelligence is used to inform security decisions, identify potential vulnerabilities, and stay ahead of emerging threats.
What is the importance of incident response planning in cyber ops?
+
Incident response planning is critical in cyber ops, as it enables organizations to quickly and effectively respond to cyber incidents, minimizing the impact and reducing the risk of further compromise.
Related Terms:
- afdp 3 12 cyberspace operations
- 3 12 afdp cyberspace ops
- air force cyber mos
- air force cyber capabilities
- air force cyber warfare
- us air force cyber operations



